HOW TO HACK ANY COMPUTER THROUGH METASPLOIT USING HIS IP ADDRESS
By hacking into your Windows 10 computer, an attacker can turn it ... powered off — and without having knowledge of their password. ... This can be very convenient for hackers who use Metasploit on a ... The Your VPS IP Here in the resource file should be changed to the IP address of the attacker's VPS. Dhanush Action Asuran
By hacking into your Windows 10 computer, an attacker can turn it ... powered off — and without having knowledge of their password. ... This can be very convenient for hackers who use Metasploit on a ... The Your VPS IP Here in the resource file should be changed to the IP address of the attacker's VPS. eff9728655 Dhanush Action Asuran
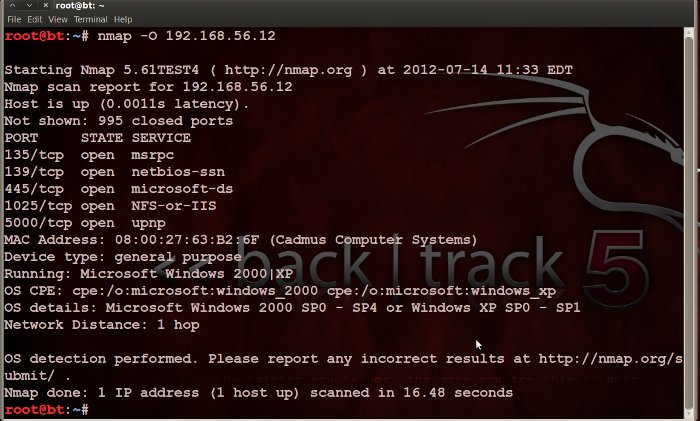
Metasploit is a powerful framework with a diverse set of tools; Using these tools attackers can easily create standalone payloads that run on fully patched .... By caching pages that have been previously requested, the proxy server ... When using a proxy server, external systems only see the IP address of the ... They may not have any specific knowledge of computer systems or why or how their hack .... It allows hackers to set up listeners that create a conducive environment ... To obtain our IP address we use the ifconfig command within Kali, ... to always connect back to us whenever the target turns on their machine (this is called ... Ethical Hacking · Hacker Training Online · Security · Computer Forensics .... Before we start hacking, let's familiarize ourselves with Metasploit so that ... It's a buffer overflow attack that enables the attacker to execute any code of their ... This will be the IP address of the remote host or the machine we're ... Schoolhouse Rock! “Electricity Electricity”